Wasabi Wallet is a Bitcoin wallet that can be very useful for a user’s privacy, but how can you be sure you’re installing the intended release?
If you’re considering using Wasabi or already have, installing malicious software from a scam website that can steal your bitcoin is the last thing you want. So what are Wasabi’s code signature strategies which can allow you to verify the authenticity of the software? For Windows and Mac, Wasabi uses the respective code signing standards that depend on centralized certificate authorities for signature validation. For every OS (Linux included), you can verify the release signature using PGP but should validate that the PGP key is really in the hands of Wasabi by leveraging a concept called Web of Trust.
This article will explain how Wasabi Wallet’s three code signing strategies (Windows, MacOS, and PGP) work and how they compare in terms of user experience, trust models, cryptography, and certificate subscription/expiry. Then, we will explain deterministic builds, why they are important, and how MacOS code signing ruins it for their platform. Finally, we will touch on Wasabi Wallet’s automatic software updater, which is only available for MacOS and Windows and employs code signature verification before installing the new release.
What is Code Signing, and Why is it Important?
The power of code is limitless. It can be used for good or malicious intent, so you should always be careful what software you install on your devices. This applies particularly if you’re interested in bitcoin, privacy, and security, which we assume you are, given that you’re reading this. This section will explain code signing and its cruciality for secure software development and distribution.
When you install open-source software on your machine, you can do it by compiling it from the source code, and you can read every code line to ensure that you understand what is happening on your machine. However, this is an extremely long and complicated process. In most cases, you might trust the open-source software development process and the team behind it, so you accept to install their compiled releases. The question now becomes, how can you ensure that you’re installing the original release?
Code signing fixes software authenticity validation by leveraging cryptography. It allows you, as a user, to verify that the binary you’re about to install on your device matches the one released by the software development team by comparing code signatures. We will examine how it works in Wasabi Wallet strategies: Windows, MacOS, and PGP.
How does Wasabi Wallet’s Windows Code Signing Work?
Operating system platforms like Microsoft’s Windows have a standard format to code signing, and Wasabi Wallet’s security engineering management team follows that. Authenticode is the platform’s code-signing technology to identify the publisher of signed software.
When a new version is released, the team uses SignTool to sign the .msi installer with an EV (Extended Validation) digital certificate issued to zkSNACKs LTD, the company maintaining Wasabi Wallet’s software development by Digicert Inc, a renowned CA (Certificate Authority).
To obtain the hardware token-protected certificate, zkSNACKs LTD underwent a multi-step identity verification process. The release gets signed with the SHA-256 algorithm, and this action is timestamped to Digicert’s servers. The current certificate was issued on February 15th, 2023, and expires on February 15th, 2025.
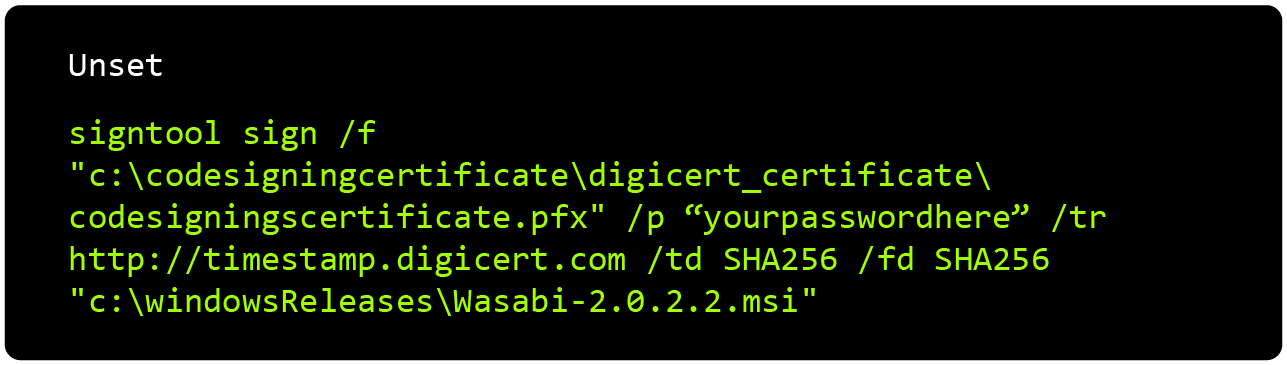
Now that we’ve established Wasabi Wallet’s Microsoft code signing strategy, let’s move forward to the other proprietary operating system platform, MacOS.
How does Wasabi Wallet’s MacOS Code Signing Work?
MacOS code signing policies are even stricter than Windows; there’s only one option available for Wasabi Wallet’s team. They have an Apple developer account on Xcode, where Apple Inc issues a developer ID certificate that signs every release. The signed package of files is sent to Apple, which signs it, too, creates a .dmg binary, and sends it back.
zkSNACKs signs the newly created .dmg binary, and it’s sent back to Apple for a final signature and notarization, in which they run many security tests on the code. Every signature uses the SHA-256 hashing algorithm.

The final code signature strategy Wasabi Wallet’s team employs is PGP code signing, which we’ll look at now.
How Does Wasabi Wallet’s PGP Code Signing Work?
Since Linux is a libre open-source operating system, there’s no standard code-signing method for your software to pass the system’s security checks. Wasabi Wallet uses the PGP (Pretty Good Privacy) standard for code signing on Linux, but it’s also available as an additional security verification step on MacOS and Windows.
PGP is an encryption program to sign, encrypt, or decrypt text, files, e-mails, etc. In this case, Wasabi Wallet’s security engineering management team uses PGP to sign their releases for all three major operating system platforms with RSA 2048-bit keys. Wasabi Wallet’s current PGP key fingerprint is 6FB3872B5D42292F59920797856348328949861E, and it is valid from the 22nd of August 2019 to the 24th of February 2028.
A user verifies the code signature by importing zkSNACKs PGP public key, downloading the latest version and the corresponding signature file, and verifying that everything matches. Find out more on how to do this here. Now that the details of each code signing strategy employed by Wasabi Wallet’s team are understood, let’s compare them.
How Do Wasabi Wallet’s Code Signature Strategies Compare Between Them?
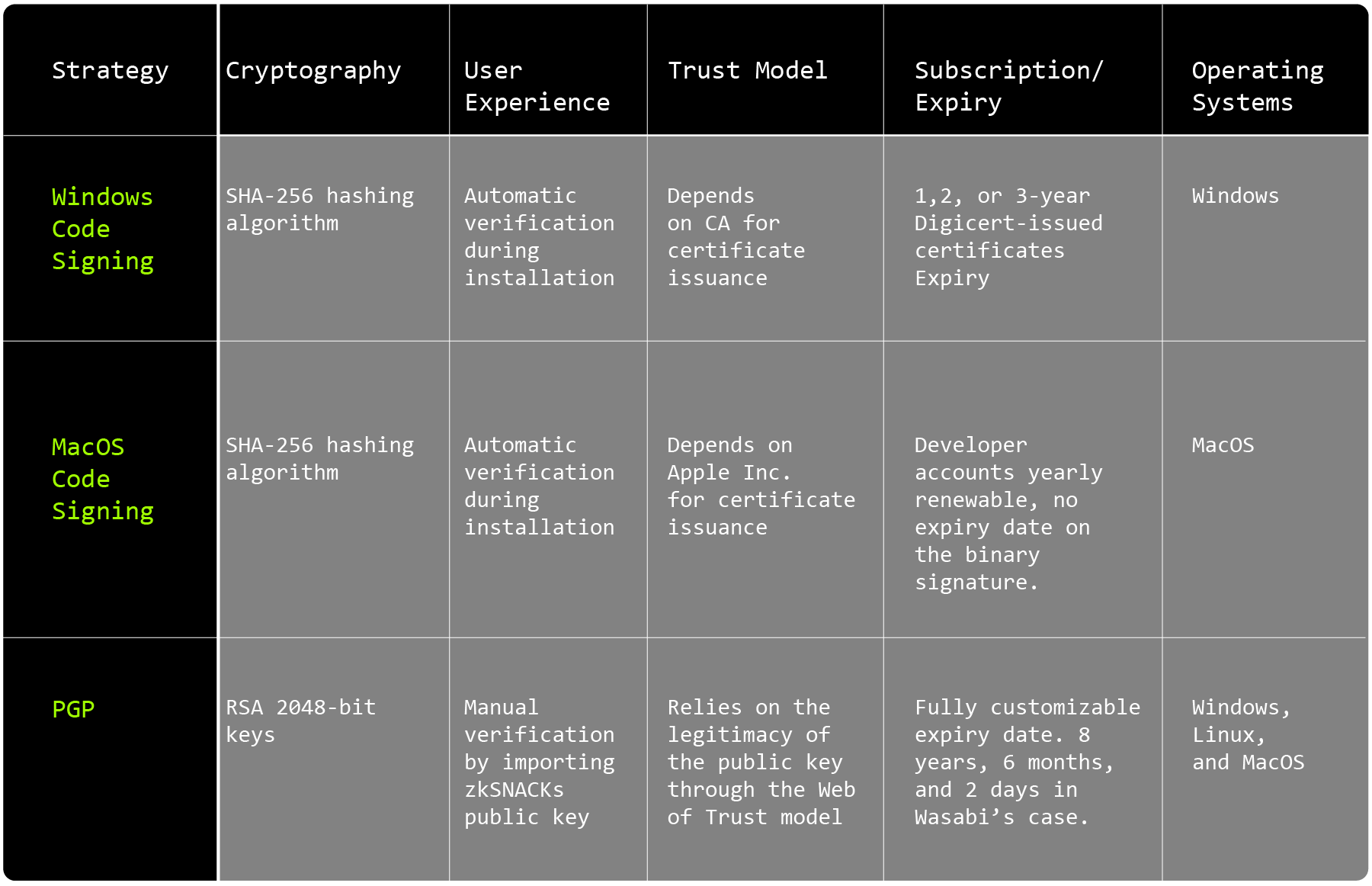
This section will compare all three code signing strategies regarding cryptography, user experience, trust models, and certificate subscriptions/expiry. First, for Windows and Mac, Wasabi Wallet uses SHA-256 as a hashing algorithm to sign the releases. For PGP, it is RSA 2048-bit keys that sign the code binary.
As a user, your experience is about the same when verifying signed releases; it’s all done automatically by your operating system during installation. On the other hand, PGP requires manual verification by importing zkSNACKs public key because it doesn’t depend on a CA (Centralized Authority) for certificate issuance, which brings us to the next point.
The trust model of PGP makes it unique compared to the other two code-signing strategies employed by Wasabi Wallet. Windows and Mac code signing depend on a CA for certificate issuance, so a user must trust that centralized entity’s legitimacy. Wasabi had a choice between many CAs on Windows, but on MacOS, you have to use the computer manufacturer and operating system developer, Apple Inc, for certificate issuance.
For PGP, the trust model simply relies on the legitimacy of the public key. How can you be sure the software development team behind Wasabi’s Wallet owns this key? To answer this question, the Web of Trust model comes into play; users must sign each other’s public keys to establish trust. Many developers have signed zkSNACKs public key with their own PGP key, so if you can physically verify the ownership of one of those PGP keys, you can trust the legitimacy of zkSNACKs PGP key. This step is optional, but you can never be sure by skipping it, and you’re under a false sense of security.
Finally, since PGP doesn’t rely on a centralized authority, it requires no permission, and its expiry date is fully customizable: in Wasabi’s case, it lasts eight years, six months, and two days. Companies like zkSNACKs can buy DigiCert-issued windows code signing certificates for 1, 2 (Wasabi’s case), or three years, costing 570 to 699 USD a year. MacOS developer accounts cost 99 to 299 USD for a yearly membership, and the key expiry date is not on the binary signature.
Now that we’ve compared the three code signing strategies used at Wasabi for releases, let’s explain what a deterministic build is, why it is important, and how MacOS code signing limits it for their platform.
What is a Deterministic Build, And Why is it Important?
Open-source software released as binaries, such as Wasabi Wallet, is signed to ensure its authenticity to the users. However, how can a user or a security auditor ensure that the binary releases match the code repository? Deterministic builds fix precisely that, and they’re essential to an open-source community to create an independently-verifiable path from source to binary code.
To build Wasabi Wallet deterministically, you must follow many steps, such as asserting the correct environment by having the same operating system and installing identical software package versions. You must then reproduce and verify builds by comparing them with the binary code. The deterministic build process works well for Windows and Linux releases, but users can’t do it for macOS because of the code signing.
How does MacOS Code Signing Limit Deterministic Build?
Unlike Windows, the binary file stores the MacOS code signature. When trying to build Wasabi Wallet on macOS deterministically, a user won’t be able to verify that the source code matches the .dmg release because he doesn’t have the certificate to sign it. However, since Wasabi Wallet’s version 2, every release includes a macOS .zip folder that one can reproducibly build with the source code.
We proceed to the final section before concluding this article: Wasabi Wallet’s automatic software updater.
What is Wasabi Wallet’s Automatic Software Updater?
On Windows and MacOS, you can turn on Wasabi Wallet’s automatic software updater. When a new update is available, the latest version will automatically download and install by the update manager. Since this isn’t a fresh install, Wasabi Wallet’s three code signing strategies aren’t employed. However, this remains safe because the code’s signature is cryptographically verified before the update.
How does the Update Manager Validate the Code it Installs?
The update manager downloads the SHA256SUMS.asc and SHA256SUMS.wasabisig files, and on line 215 of this code file WasabiSignerHelpers.VerifySha256SumsFileAsync is called to validate the signature. Then on that function in the WasabiSignerHelpers code file, the content and signature files are read and evaluated to match the constant Wasabi’s Public Key on line 38.
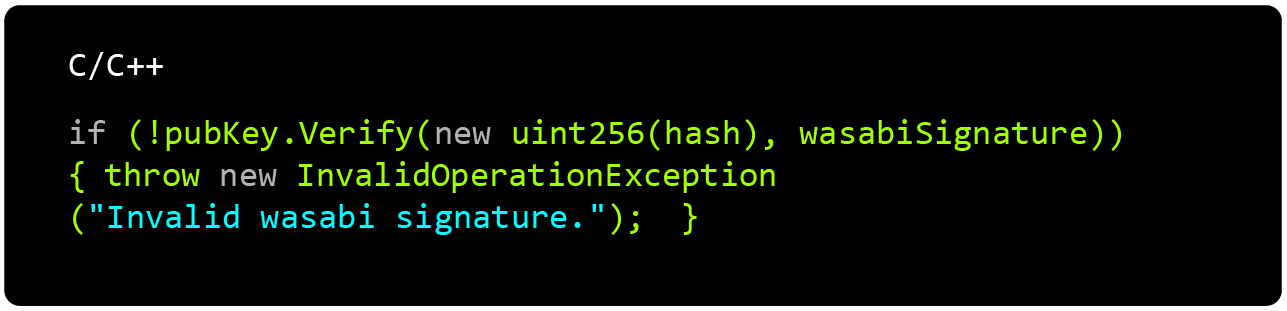
In simple terms, the binary hash and the digital signature are downloaded, and then, the code verifies that Wasabi’s signature matches the hash, and matches the public key saved in the previously installed version. This key set differs from all other code-signing keys used; it uses the same cryptography as Bitcoin.
Conclusion
In this article, we explained what code signing is, why it is essential, and what the three code signing strategies used for Wasabi Wallet’s releases are, which we compared in terms of cryptography, user experience, trust models, and certificate subscription/expiry. Then, we defined what a deterministic build is, why it is important, and how MacOS code signing clashes with it. Finally, we describe the code signature verification happening when automatically updating Wasabi.
PGP code signature verification is recommended to all users, even those on Windows and Mac, because, unlike the other code signature strategies, it is trustless if employed correctly by leveraging the Web of Trust and physically validating a key that has validated the zkSNACKs key. It is also essential to be wary of scam websites, which might resemble the domain name.
You should only install software from the official website https://wasabiwallet.is and the official onion service.


